Technical IT Security for Proactive Defence
Next Offering
Inquire below for future program dates.

Understand and apply IT Security practices, techniques and apply technical hands on exercises for proactive cyber defence for the business environment.
Technical IT Security for Proactive Defence is a hands-on technical course for security teams. This course addresses modern threats, debunks the myths about cyber attackers and enables threat hunting that goes beyond passive detection technology, waiting for SIEM rules to fire, and strengthens incident response.
Participants will learn proactive IT Security defence - threat hunting using MITRE ATT&CK, applying threat intelligence Indicators of Compromise (IOCs), TTPs (Tactics, Techniques and Procedures), network and common operating system hardening, vulnerability assessment and prioritizing patch management approaches, defend and respond to incidents involving Ransomware.
Key Learning Outcomes
- Application of knowledge through technical hands-on lab exercises
- Recognize technical elements of an attack, and mapping related controls
- Map modern attack TTPs to MITRE ATT&CK Framework for top SIEM rules
- Identify and implement vulnerability scanning at scale, with priority
- Apply actions from threat intelligence for prioritized security defence
- Navigate a real-world incident response scenario to respond to Ransomware
Course Duration: 2 days | Continuing Education Contact Hours: 14
Participant Experiences
"Dean is extremely knowledgeable in the field of cybersecurity which adds a lot ofvalue to the course. This course is invaluable to anyone looking to strengthen the securityposture of their organization".
Course Endorsements and Partnerships
This course has been endorsed by techNL as a valuable professional development option for member organizations.
___________________________________________________________________
This course qualifies for Professional Development Units (PDUs) as defined by the Project Management Institute (PMI).
Each course has a specific qualifying factor for PDUs. See the table below for a specific PDU breakdown for this Gardiner Center program.
To learn more about PDUs and how to apply these credits to your active credential please see www.pmi.org.
|
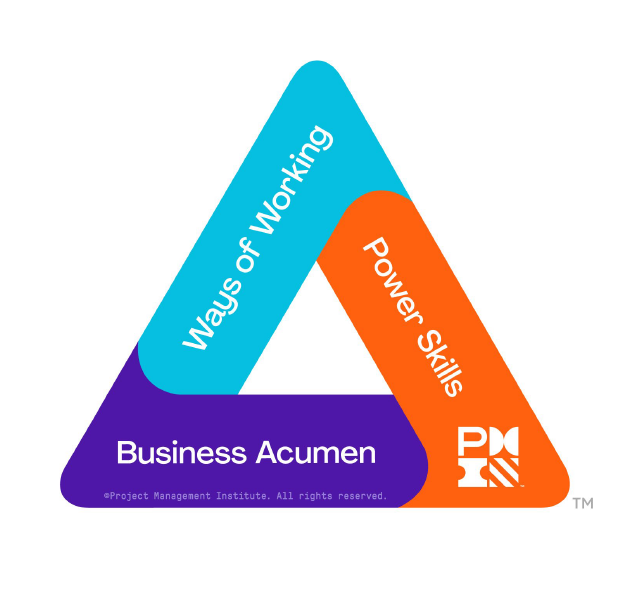
Talent Triangle Allocations |
Qualifying PDU Hours |
|
|
Ways of Working |
7.2 |
|
|
Power Skills |
0 | |
|
Business Acumen |
0 | |
|
TOTAL |
7.2 |
Who Should Attend
This course is well suited for those in IT Security or cybersecurity defense roles across cyber incident response, security operations / SIEM analysis, threat analysis, and vulnerability assessments.